The Best Smart Locks of 2024
Smart locks use Bluetooth and other wireless technologies to give you keyless locking and unlocking. Go keyless with Safe Home’s tips about the best smart locks.


- Total integration with Google Home lets you use your voice to control your front door
- Easily installs with nothing more than a screwdriver
- With no slot for a key, this lock can’t be picked

- Lets you use a backup key if you should ever forget your pin code
- Create custom pin codes so you can keep track of who comes and goes
- Security brand with over 100 years in the business

- Get into your home by simply tapping a lock as long as you’re carrying the key fob
- Give digital keys to family and friends so they can get in when they need to
- Can install to work with your original lock and key


The best smart locks of 2024 let you go keyless in different ways. Here we share popular smart locks that allow control with PIN touchscreens, a single tap, your voice, and mobile apps. Some smart locks let you keep using traditional house keys as a backup too.
Smart Lock Features We Tested
| Remote lock/unlock | App-based control |
|---|---|
| Automatic lock | Location-based |
| Voice control | Alexa, Google Assistant, Siri |
| Keyless entry | PIN, touch control |
There’s no “best smart lock” for everyone. If you rent a home or apartment, for example, you’ll probably need a smart lock that can work with the door’s original key. If you own the property though, you might prefer a completely keyless smart lock system. Here we review the best smart locks in both categories.
Whether keyed or keyless, a smart lock can generally be installed in about ten to 15 minutes. Installation is straightforward except when doors are extra thick and hardware needs to be adapted.
Who makes the best smart locks? Traditional security companies have joined the game: Kwikset, Schlage, and Yale are now among the best smart lock providers. We cover their products along with impressive locks from the newcomers August and Nest.
Jump ahead to our reviews of specific smart locks, or read straight through for a bit of general education… Smart Locks 101! Learn basics about smart locks before you buy.
About Smart Locks with PINs, Touch & Voice Control
The best smart locks can be controlled multiple ways. Most common is using a PIN (personal identification number) with the lock itself, or remotely with your cell phone. You can also lock/unlock doors with a quick touch or by voice.
About Smart Lock PINs
A smart lock PIN is typically four or five digits. To unlock a door you can tap your PIN on the smart lock’s small touchscreen. When you’re away from home, you can use the same code with a mobile app to accomplish remote locking and unlocking. The best smart locks have their own mobile apps and also work with apps for popular home security companies such as ADT, Frontpoint, SimpliSafe, and Vivint.
As the account owner, you can assign unique PINs to each family member, dog walker, babysitter or nanny, etc. For extra security the best smart locks let you set schedules for particular PINs, and of course, you can disable a PIN anytime. You can track PIN use with a mobile app and get text notifications about the activity.
How many PINs can you assign? Some smart locks have small PIN limits; you might get a dozen slots for temporary and permanent codes. Other locks are made with the hospitality industry in mind. These security gadgets let you set an unlimited number of temporary or permanent codes. Smart lock mobile apps let you easily share the digital keys by text or email.
Other Types of Smart Lock Control: Touch and Voice
Instead of PINs, or in addition to PINs, some of the best smart locks respond to touch: Just tap a lock to disengage the deadbolt. This seemingly magical technology works when you’re carrying a keyfob that’s connected to the system. The fob works within a few feet of the smart lock, so you won’t need to actually remove it from your wallet or bag. Obviously, this setup can be useful if you arrive home with arms full of groceries, your children, etc. The same smart locks let you quickly re-lock with a tap too.
Amazon Alexa and her virtual personal assistant friends can also help out. The best smart locks respond to questions like “Hey Siri, is my front door unlocked?” and commands like “Alexa, lock the front door.” You can also unlock some devices by voice, although this requires saying your PIN aloud. Obviously it wouldn’t be wise to keep a PIN active if you might be overheard… but as mentioned above, you can change the PIN anytime you like.
Now, our nominee for best smart lock overall! The Nest x Yale Smart Lock lets you set PINs with two access levels. People with Family status can set PINs, view account activity, and invite other users. People without Family status receive PINs that are designated Home Entry Only.
Best Smart Locks of 2024
- Nest x Yale - Best Smart Lock Overall
- Schlage Connect - Best Wi-Fi Smart Lock
- Kwikset SmartCode 913 Deadbolt - Best Bluetooth Smart Lock
- August - Best Z
- Yale Smart Locks - Best Touchscreen Smart Lock
A Detailed List of the Best Smart Locks
-
1. Nest x Yale - Best Smart Lock Overall
Nest is a Google-owned company that sells security cameras and standalone smart home components. Their Nest x Yale Smart Lock ($279) is a best Wi-Fi smart lock overall for exclusively keyless unlocking with a PIN. Keyless locking is even easier with a single tap on the hardware! All in all the product is an impressive collaboration between young and old home security brands.
Nest – Best Smart Lock Overall
Nest is a Google-owned company that sells security cameras and standalone smart home components. Their Nest x Yale Smart Lock ($279) is a best Wi-Fi smart lock overall for exclusively keyless unlocking with a PIN. Keyless locking is even easier with a single tap on the hardware! All in all the product is an impressive collaboration between young and old home security brands.
Some other perks with the Nest x Yale device are door lock reminders and a smartphone connection. If you have a Google Home speaker, you’ll have voice control over Nest x Yale smart locks too.
You can use Nest smart locks with a Nest Secure home security system (no longer sold by Nest), or else connect it to your home Wi-Fi network via a plug-in gadget called Nest Connect ($69).
Minimalist Modern Style
The aesthetics of Nest x Yale Smart Lock can complement virtually any home. The lock has a black oval touchscreen with simple metal casing, and you can choose from three finishes (Oil Rubbed Bronze, Polished Bronze, and Satin Nickel). The screen stays dark until your hand makes contact and illuminates the keypad numbers with soft white backlighting.
Tamper proof, the lock will disable for a minute after five incorrect PIN attempts. You can receive alerts on your phone and get real-time notifications of possible shenanigans. If you have a Nest Hello doorbell cameras, then you’ll also see who’s attempting to gain entry.
Pros
- Totally keyless; no picked locks!
- Owner can tap lock to move bolt
- Can attach schedules to PINs
- Tamper lockout after five incorrect PIN attempts
- Remote locking/unlocking with free Nest app
- Can track entries with Nest app
- Lockup reminders and auto-lock option
Cons
- Not compatible with security systems besides existing Nest Secure systems, which are no longer available on the market
- Without Nest Secure requires $69 Nest Connect (a Wi-Fi bridge) for self-monitoring
Nest Lock Installation Requirements
Using the Nest x Yale lock requires 1) home WiFi and 2) a mobile phone with Bluetooth and the Nest app for iOS or Android.
- The Nest smart lock can connect to WiFi automatically if you already have a Nest Secure alarm system.
- Without a Nest Secure home security system, you’ll need a Nest Connect. Nest Connect is a $69 plug-in device that lets Nest locks communicate with your home WiFi network.
The lock will fit standard interior and exterior household doors that are 1⅜” to 2¼“ thick. The only tool needed for installation is a Phillips screwdriver. A pencil and masking tape can make the job easier. Installation videos are on YouTube and the Nest website.
Nest Lock Batteries
The Nest smart lock is powered by four AA batteries. Typically a set of Nest lock batteries will serve for about a year.
To avoid getting locked out of your house, listen to your lock! It starts to send low battery alerts five weeks before a change is critical. However, if you do get locked out because of drained batteries, you can externally recharge the system by connecting a 9v battery. This feature helps make Nest one of the best smart locks on the market; competitors don’t have an external charge solution.
Verdict
The Nest x Yale smart lock is recommended for homes with and without Nest Secure home security, a product that Nest has discontinued. Totally keyless, it makes your doors “unpickable” and has tamper lockout after incorrect PIN attempts… And Nest isn’t just about security; touch control and voice control help streamline your day.
Purchased directly from the Nest website, this overall best smart lock of 2024 carries a two-year warranty on parts and labor.
-
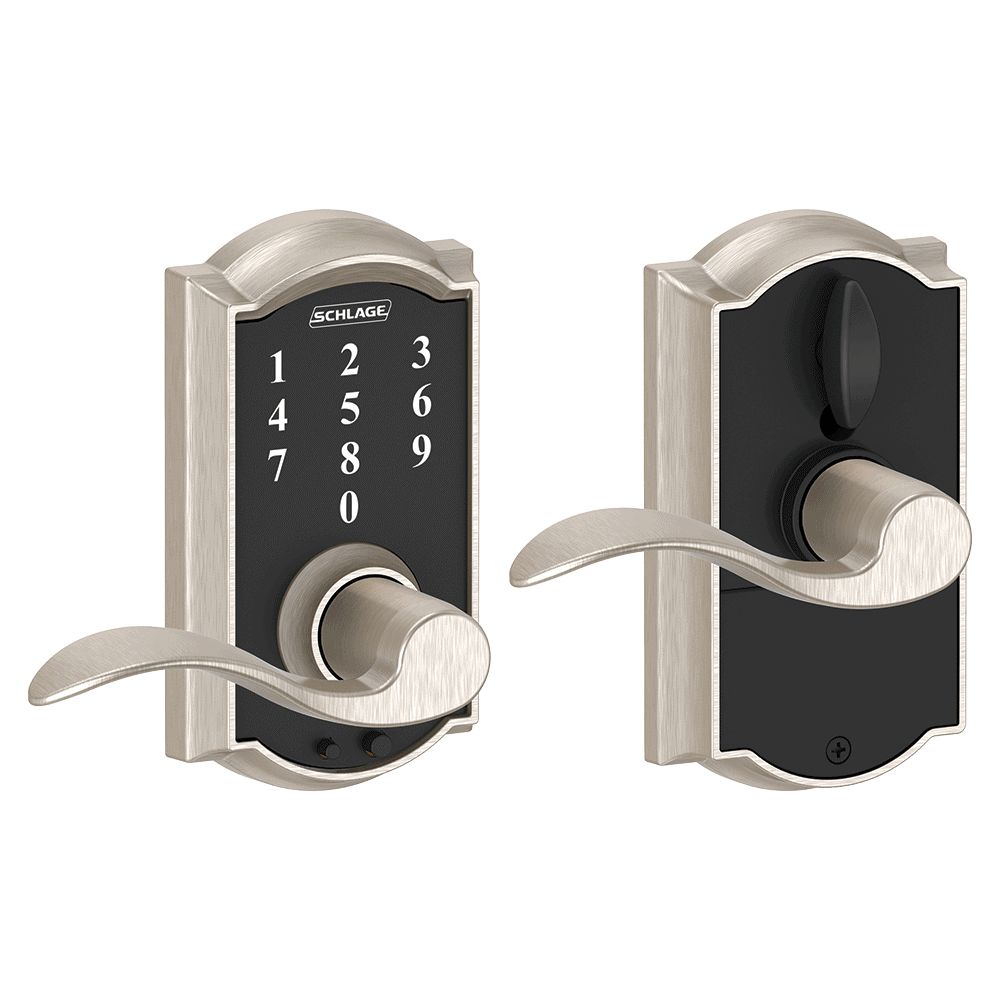
2. Schlage Connect - Best Wi-Fi Smart Lock
Schlage has been in the lock business since 1920. This heavy-duty brand is trusted by banks as well as renters, homeowners, and property managers. One of their bestselling smart home products is Schlage Encode ($249), a deadbolt lock with its own Wi-Fi system.
Schlage – Best Wi-Fi Smart Lock
Schlage has been in the lock business since 1920. This heavy-duty brand is trusted by banks as well as renters, homeowners, and property managers. One of their bestselling smart home products is Schlage Encode ($249), a deadbolt lock with its own Wi-Fi system.
Schlage Encode has a touchpad and also accepts a physical key. If someone tries to defeat the alarm, a siren will sound. Overall Schlage Encode is our nominee for best Wi-Fi smart lock that doesn’t require a home security hub.
Also for sale are Schlage Sense, which works with Apple HomeKit, and Schlage Connect, which works with any Z-Wave home security system.
Summary of Schlage Smart Lock Benefits
Schlage Encode is easily installed and extremely durable. You can remotely interact with this smart lock via your mobile phone and/or with Amazon Alexa commands. WiFi is built into each lock itself, so you won’t need a separate home Wi-Fi network for monitoring.
Pairing with a mobile app (either Schlage Home or Amazon Key) lets you set up to 100 customized access codes, seamlessly share them by text or email, and know whenever they’re used.
Pros
- Wi-Fi is built in; security or home automation hub not required
- Works with physical key
- Allows up to 100 PINs
- Siren reports tampering
cons
Complaining isn’t easy! Schlage Encode is all-around impressive. It’s a top option if you want smart lock features but think it’s wise to keep your physical key in action too.
A minor complaint is that you don’t get the option of auto unlock as you approach a door. Automatic unlocking (when your phone or fob is present) is an option with Kwikset Kevo as described above.
Schlage Encode Installation
Installation for Schlage Encode takes about 10 to 15 minutes with no tool required but a Phillips screwdriver. A snapshot of installation on the Schlage website conveys how simple the setup process can be.
Four AA batteries will power a Schlage lock for about six months with normal use. An icon on the lock’s touch screen will flash when battery power is low.
-
3. Kwikset SmartCode 913 Deadbolt - Best Bluetooth Smart Lock
Kwikset has specialized in locks since the 1940s. One of their newer lines, Kevo, features battery-powered smart locks that can replace or upgrade traditional deadbolt locks. As the account owner you can just tap a lock for home access! Kwikset Kevo is the best Bluetooth smart lock line that works with a wide range of home security systems as well as independently.
Kwikset – Best Bluetooth Smart Lock
Kwikset has specialized in locks since the 1940s. One of their newer lines, Kevo, features battery-powered smart locks that can replace or upgrade traditional deadbolt locks. As the account owner you can just tap a lock for home access! Kwikset Kevo is the best Bluetooth smart lock line that works with a wide range of home security systems as well as independently.
Kevo locks can be seamlessly integrated with home security systems by ADT, existing Nest Secure systems, SimpliSafe, Scout, and lots of other companies. They’re also compatible with Amazon Alexa for voice commands. For instance, “Kevo, ask Alexa to unlock Studio Apartment Door.”
To Key or Not To Key?
Totally keyless options from Kwikset Kevo are top competitors with the Nest x Yale lock above. Furthermore Kwikset has a smart lock called Kevo Convert that keeps your original key active.
Kevo Contemporary and Traditional locks ($199) are among the best Bluetooth smart locks with military-grade encryption. These locks are identical to each other except for aesthetics; Kevo Contemporary is square-shaped and Kevo Traditional is a circle lock. Both styles can make your doors totally keyless. When your phone with Bluetooth is in range of a lock, you can control the deadbolt by touch; just tap the metal casing to lock or unlock. You can also go phone-free and just carry a lightweight Kevo fob ($26) for tap control.
Kevo Convert ($149) gives the benefits of Bluetooth connectivity while keeping your door’s original key system intact. The exterior of your door lock doesn’t change, and the interior can receive PINs via smartphones. Kevo Convert is a handy option for AirBnb rentals and other properties with frequent short-term guests. The Kevo smartphone app makes it easy to send digital keys and track their use.
A Kevo lock purchase includes a lifetime warranty on the finish and mechanical parts, and one year on the electronics.
Pros
- Available key-free or with virtually unpickable locks
- Owner can tap lock to move bolt
- Can schedule eKeys for non-residents
- Mobile notifications of PIN use
- Allows remote locking/unlocking with free Kevo app
- Compatible with Alexa and many home security system brands
Cons
- Batteries may drain quickly
Verdict
Kwikset Kevo has big appeal whether you want exclusively keyless entry or want to retain your door’s original key, and whether or not you have a full home security system. The totally keyless options are called Contemporary and Traditional. The smart lock with PIN codes and physical key is called Kevo Convert.
Note: Kwikset Kevo locks are for standard door sizes only. Conversion kits aren’t available, so confirm that your door is 1⅜” to 1¾” thick before you buy a Kevo lock.
-
4. August - Best Z
August Home is a manufacturer focused on Z-Wave locks and doorbell video cameras. Their smart locks are practical for renters as well as homeowners, as they let you use your original house key as backup to keyless entry. The August Smart Lock Pro has big appeal for rental property managers too, as it lets you set unlimited temporary and permanent PINs. Compatible mobile apps let you see door status (locked/unlocked), track activity, and set access codes.
August – Best Z-Wave Smart Lock
August Home is a manufacturer focused on Z-Wave locks and doorbell video cameras. Their smart locks are practical for renters as well as homeowners, as they let you use your original house key as backup to keyless entry. The August Smart Lock Pro has big appeal for rental property managers too, as it lets you set unlimited temporary and permanent PINs. Compatible mobile apps let you see door status (locked/unlocked), track activity, and set access codes.
The August Smart Lock Pro ($199) takes the title for Best Z-Wave Smart Lock. It’s packaged with a Wi-Fi Bridge, which lets you use the smart lock without a home security hub. It can integrate with Z-Wave and also non-Z-Wave security systems. Among the many brands compatible with August smart locks are ADT, Frontpoint, SimpliSafe, and Vivint.
Smart Lock Pro has Apple HomeKit compatibility too. This allows control by Siri, iPhone, iPad, and Apple Watch. Prefer a different virtual assistant? Alexa and Google Assistant work with August too.
About the Power
Two AA batteries power the lock. When power drains to 20 percent, you’ll receive a low battery notification by email. Icons on the lock and within the August Home app also indicate low battery status. With regular use a set of batteries should last about four to six months. This fact gives August a slight disadvantage, as competitors use four batteries for twice the convenience. Still… August locks are darn convenient!
All in all the August Smart Lock Pro is an exceptionally flexible home security gadget. You can monitor it through the August Home app or via many other platforms. For most shoppers the main potential drawback to consider is width; on some doors there isn’t enough room for installation. The device needs a 4.75” space above a doorknob, as shown on the August website.
Pros
- Has a Wi-Fi bridge; security hub not required
- Works with Z-Wave and non-Z-Wave security systems
- Compatible with Alexa, Google Assistant, and Siri
- Unlimited PINs
- Door Sense indicates open/closed status
Cons
- Too wide for some doors
August Lock Installation
Do-it-yourself installation of August locks is straightforward. Smart Lock Pro arrives with nine adapters to be compatible with just about any existing door lock. The setup process takes about 10 to 15 minutes, and the only tool you’ll need is a screwdriver.
Comprehensive photos of the setup process are at the August Home website.
-
5. Yale Smart Locks - Best Touchscreen Smart Lock
Established in the 1860s, Yale is the oldest lockmaker in this smart lock review. Their new Yale Assure smart lock ($149) shows that the brand stays relevant in the wireless age. Yale Assure is a completely keyless lock with PIN entry and one-tap locking. Loaded with smart features, it’s the best touchscreen lock that can work independently with an app or integrate with a Z-Wave or Zigbee hub. If you opt for a Z-Wave or Zigbee hookup, the total Yale Assure price moves from $149 to $199… still a competitive payout for a top-rated smart lock system.
Yale – Best Touchscreen Smart Lock
Established in the 1860s, Yale is the oldest lockmaker in this smart lock review. Their new Yale Assure smart lock ($149) shows that the brand stays relevant in the wireless age. Yale Assure is a completely keyless lock with PIN entry and one-tap locking. Loaded with smart features, it’s the best touchscreen lock that can work independently with an app or integrate with a Z-Wave or Zigbee hub. If you opt for a Z-Wave or Zigbee hookup, the total Yale Assure price moves from $149 to $199… still a competitive payout for a top-rated smart lock system.
Yale Assure is enabled for HomeFit as well. This means you can take control by iPhone, iPad, Apple Watch, and Siri.
Yet another perk is that Yale Assure has an IFTTT channel. What is IFTTT? The abbreviation means “If This, Then That.” If your Yale smart lock has action, it can trigger another home automation device. For instance, unlocking your front door can trigger a hallway light.
The Look
The Yale Assure lock looks similar to the Nest x Yale locks shown above. It features a small touchscreen with rounded edges and metal trim with satin nickel, matte bronze, or shiny bronze finish. Touching the screen activates white backlighting for the keypad.
PINs, Auto Re-Lock, and Tamper Siren
You can set up to 250 PINs with the Yale smart lock. After you enter your home with a PIN, you can have the door automatically lock behind you in 30 seconds with Auto Re-Lock. You can also simply tap the lock casing to move the deadbolt.
For extra PIN security you can engage Shutdown Time, which disables the lock for 60 seconds after five consecutive wrong PINs. If the lock is connected to a camera system, then Shutdown Time is prime for streaming live video and maybe dispatching police! The Yale lock has All Code Lockout mode too, which disables all user codes except the Master.
Tamper alert is always active on Yale smart locks. This feature will sound a siren if someone tries to damage the hardware.
Pros
- Z-Wave and Zigbee compatible
- HomeFit compatible
- IFTTT channel
- One-touch locking
- Tamper siren
- Shutdown Time and All Code Lockout modes
- Up to 250 PINs
Cons
- No physical key
The keyless aspect of a smart lock is both a positive and a negative. On the up side, there’s no lock to pick! On the down side, you’ll need another entryway (or a locksmith) in case the batteries drain or there’s a power outage. A great alternative: Yale makes a lock called YRD226 that’s identical to Assure except it has a keyway.